From Prompt to Collector to Structured Output
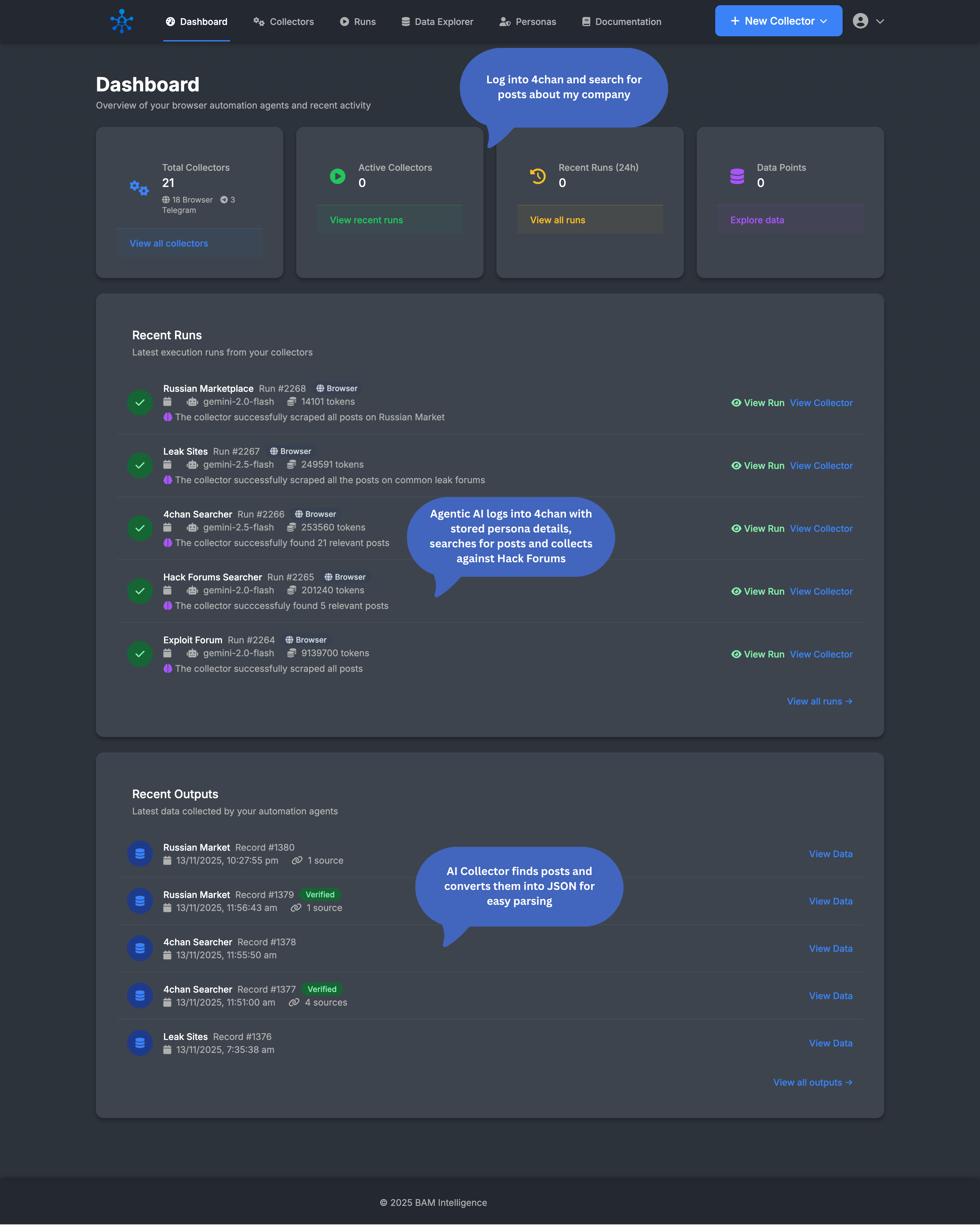
Create collectors with natural language prompts
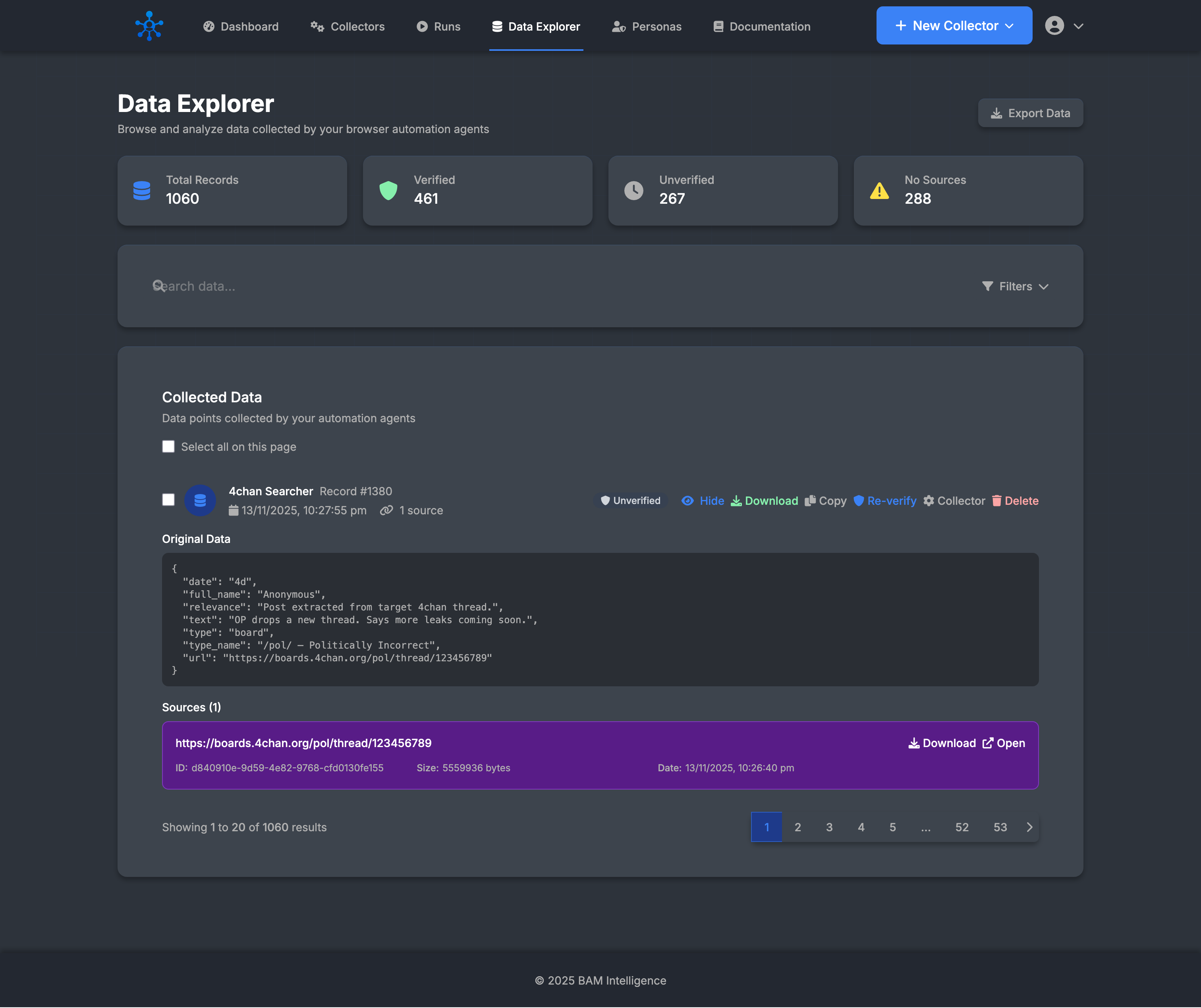
Get structured, verified intelligence outputs
Describe what you need. BAM's agentic AI collects the web, navigates private platforms, and gives you structured intelligence.
Natural-language prompts powered by any frontier model.
Human-like browsing, personas, authenticated sessions, private platform access.
Normalized outputs, export-ready JSON that has been verified against source documents.

Create collectors with natural language prompts

Get structured, verified intelligence outputs
Autonomous agents execute multi-step collection tasks across any website or private community with verification of outputs against the original sources to support the warrant process.
Propietary human-like browsing technology
Avoids CAPTCHAs, bot detection, and fingerprinting. Operates as a believable human persona.
AI-driven collection on platforms where real threat activity happens: Open, Deep, Dark web and private communities such as Telegram, forums, marketplaces, leak sites, closed communities.
Manage multiple identities and authenticated sessions for deep and dark web access.
Transforms raw pages into clean, normalized JSON.
Run BAM with your preferred LLM in secure environments on premise or in the cloud.
Supports all major frontier models — cloud or on-prem.
View exactly what the agent did: navigation steps, decisions, errors.
Monitor forums, marketplaces, leak sites, ransomware portals.
Brand monitoring, credential leaks, company mentions, exposed assets.
Authenticated collection in sensitive environments, with air-gapped deployment.
Join the waitlist and be among the first to experience BAM Intelligence.